



 accesses since September 27, 2010
accesses since September 27, 2010
 copyright notice
copyright notice




 accesses since September 27, 2010
accesses since September 27, 2010
In my last installment I gave two examples of some outstandingly bad IT decisions: failing to include sanitizing copier disk drives in INFOSEC policies, and a gloriously idiotic approach to data redaction by the TSA. Award contenders, all, these are the surreal examples of the CIOs art. Some of these stories found their way to become top downloads on YouTube.
Just after I submitted my last column, another egregious violation of IT security best practices came to light - the recent WikiLeaks scandal popularly called the "Afghan War Diary, 2004-2010." According to Wikileaks.org, on July 25, 2010 it released over 91,000 reports during this period, both on their website and to the press. These reports were accumulated by the U.S. Military on defense department servers from military and intelligence personnel. By all accounts they contained classified information (apparently at the "secret" level) on U.S. activities in Afghanistan on topics as far ranging as GPS maps, situation reports, political assessments, and embarrassing videos of helicopter attacks. As is fashionable, objective media coverage of the event quickly disintegrated into political bias and blame, with little professional journalism devoted to printing stories of enduring value. No Pulitzer to be found here, folks.
Figures 1 and 2 are typical of the leaked documents.
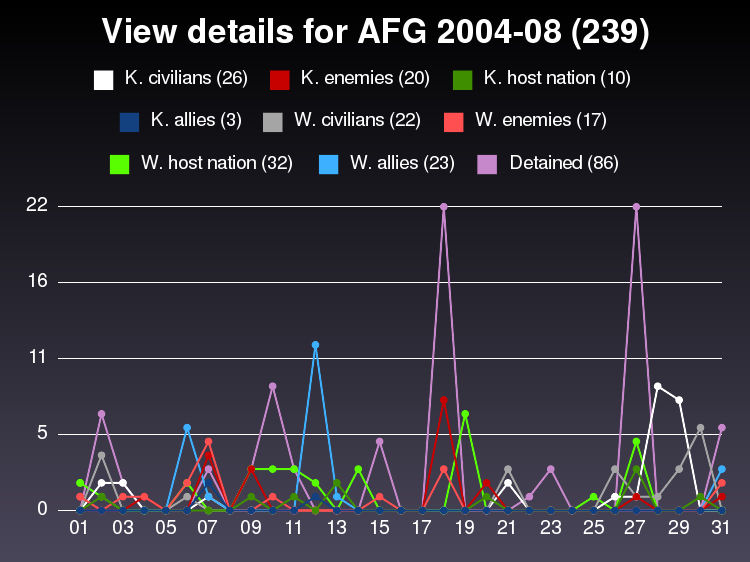
Figure 1: Randomly selected Wikileaked Graphic from the "Afghan War Diaries"
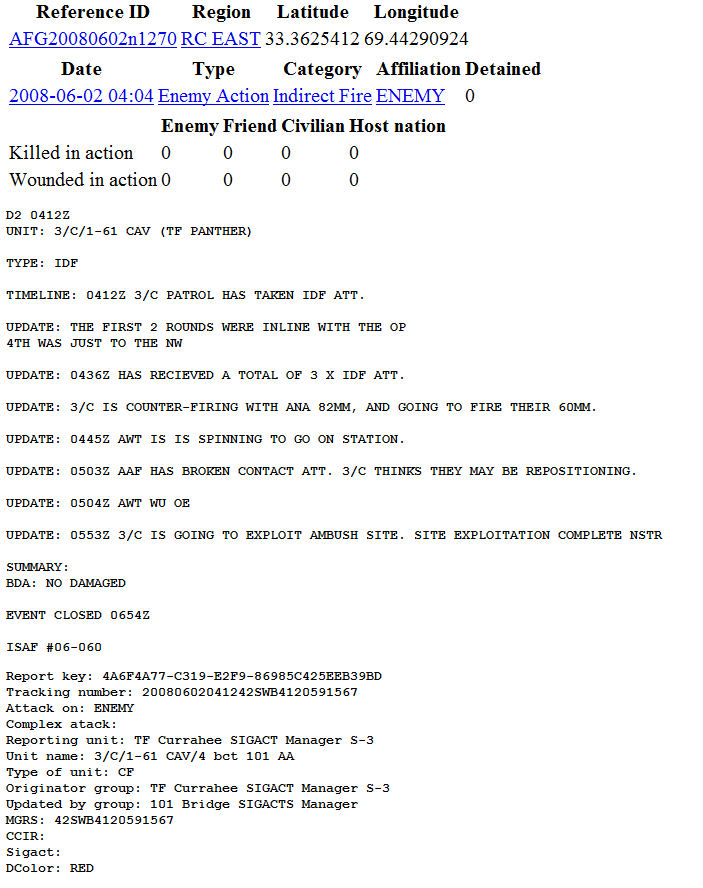
Figure 2: Typical Wikileaked document from the "Afghan War Diaries"
Our challenge is to find the "real story" behind the leaking of these documents - or, at the very least, to get pointed in the right direction.
To get at the real story, we begin with the words of the great military strategist and eyeglass manufacturer, Benjamin Franklin, who said "Two people can keep a secret if one of them is dead." In so saying, Ben became the progenitur of the modern digital-intelligence operative. Ben anticipated Wikileak's popularity by several hundred years - perhaps sometime between his discoveries that lightning was in fact electricity, and the cooling effect of evaporation. In any case, people who hold secrets don't always keep them. Ben got that. While not as familiar as the golden rule, it's truth is unassailable. Maybe the military and intelligence community should make it their "silver rule" or "bronze rule." But I'm getting ahead of myself.
According to the Guardian, these Wikileaks document is "a devastating portrait of the failing war in Afghanistan...." The New York Times said the leaks are "an unvarnished ... picture of the war in Afghanistan that is in many respects more grim than the official portrayal." This has been a very leaky year, secret-wise. Last year, some of Ambassador Karl Eikenberry's confidential communiques to the U.S. State Department were leaked. He opined that "President Karzai is not an adequate strategic partner." I've got a news flash for the Guardian, Times, and Eikenberry: a lot of folks figured this out without the help of the leaks. As a heads-up, there is no need to speculate that there isn't always a clear distinction between the Mexican government and the Mexican drug cartels. The toothpaste is out of that tube as well.
However, the leaks are deserving of close scrutiny because we can't afford to minimize the potential harm to people, citizens and military, and increased risk to families and friends due to retaliation as a result of the leaks. If there were names named, persons identified, plans spoiled, etc. we need to know the details. So while the press assessment of the leaks mentioned above may not be newsworthy, the details behind the leaks might be.
So it's appropriate to ask, if this is a serious breach of security, how did it happen and who is to blame? As near as I can tell, the journalists have completely missed this point as well. The real problem isn't in focus. Let me explain.
According to the news reports, the likely source of the leaks is a U.S. Army private named Bradley Manning (cf, bradleymanning.org) in his early 20s and currently incarcerated in Kuwait pending an Article 32 investigation of 12 counts of violating U.S. secrecy laws. Pfc. Manning is also accused of leaking the classified video of the very controversial helicopter strike in Baghdad in 2007 that is easily recovered on the Internet with the search string, "Collateral Murder." The primary witness is apparently a former hacker with a colorful and somewhat checkered legal past named Lamo in whom the Army private placed confidence before and/or during the alleged leaks. This part of the story may be discovered via any search engine and, so far as I can tell, is not disputed. The received scenario seems to be something like this: private has access to secret data, claims crisis-of-conscience, and releases secret data to media for greater good.
But the "real" story is no more about this private than the real story of Watergate is about Daniel Ellsberg.
The real story is in the search for the "source of the problem" not the "source of the leak." At this writing, the media just doesn't seem to get this. By the way, this "real story" is what ties this column to my previous on truly stupid IT decisions. The source of the problem is not an Army private, but some really idiotic military INFOSEC policies that allow Army privates unrestricted access to potentially dangerous or embarrassing secret data. Any competent executive will confirm that risk management is not about finding perfect solutions to problems. Risk management is the art of balancing risks against rewards. There is at least one very highly placed military officer somewhere who failed to comprehend this basic principle. Fortunately for the officer(s), the press doesn't understand that point either.
Something broke down either at the level of INFOSEC policy or the implementation thereof. I suspect the fault is the policy itself. There's a reason that reporters keep the identities of their sources to themselves. Same with cops and snitches. They're mindful of Ben Franklin's admonition. If sources are disclosed - e.g., on servers accessed by privates - it won't be long before there are no more sources. This isn't rocket science. You can figure this out by watching the Sopranos. So *if* there was sensitive information in the raw files, the real story is the exposure of person who authorized privates to have access to them without first redacting (aka scrubbing) the data?
Try as I may, my military friends cannot explain this egregious breach of IT common sense. I've asked several career officers at what level in the chain of command a clearance like this would be approved, but none of them seem know (at least that's what they're telling me). What's worse they apparently don't know who to ask. That's an even bigger problem. If senior career officers in several branches of the military have no idea what position in the chain of command would authorize access to sensitive raw data, leaks are inevitable.
Couched in your terms, if a regulator or SOX compliance consultant asks one of your executives where in your organization one could find the person who oversees PCI security policy and implementation, would it be acceptable for the execitive to say "I haven't a clue."? It doesn't matter whether the executive is CEO or VP for International Marketing, if they can't associate a name or title with the responsibility for keeping tabs on revenue security, the organization has some serious issues. Because IT is ubiquitous in the modern organization, when it comes to cybersecurity compliance, if everyone isn't on board, the organization by definition sill never be compliant.
So this Wikileak event might serve well as a wakeup call for all of us to revisit our "need to know" philosophy for file access. Who knows, there may be avoid a potentially embarrassing Wikileak in your organization's future.