



 accesses since June 6, 2012
accesses since June 6, 2012
 copyright notice
copyright notice




 accesses since June 6, 2012
accesses since June 6, 2012
You all remember the bygone days of the web when gratuitous media popped up everywhere. Many commentators, including myself, bemoaned the fact that this unrefined content was polluting the web. Within a few years, certainly by the mid-1990's, this cybercrap was ubiquitous, motivated by millions and millions of homepages spawned mostly by people that didn't warrant them. I remember writing columns in the early 1990s lamenting the overpopulation of “content-free” homepages.
And in 1991, this bandwidth banditry went interactive with the Trojan Room Coffee Pot (TRCP) – a precursor to the webcam. That's right, interactivity on the web didn't have its origins in video games or pornography, but coffee pots. A group of clever Cambridge University students used homegrown RPC tools, MSRPC2, that ran over the MSNL protocol designed for ATM networks. Every second a JPG of the coffeepot was captured and made available online through MSRPC2. All to save the researchers an unsatisfying climb up a few flights of stairs.

FIGURE 1: The Original Trojan Room Coffee Pot – perhaps the world’s first webcam prototype (circa 1991)
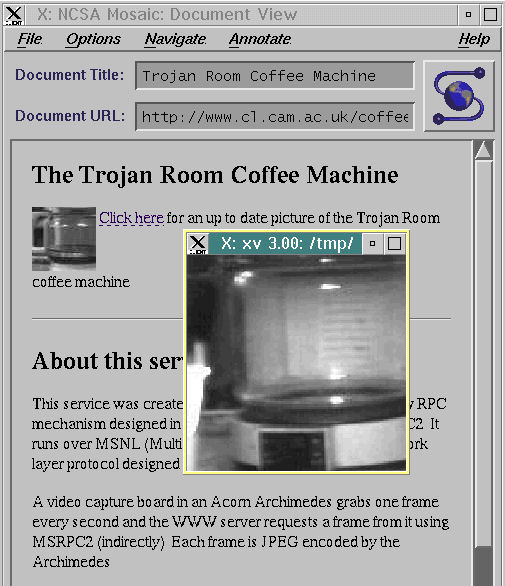
FIGURE 2: The ‘Nexgen’ Trojan Room Coffee Pot on the Web (circa 1993) [note the NCSA Mosaic browser – no Firefox or Internet Explorer in those days!] )
The original primitive frame-grabber setup went away in a few years, because the web had by 1993 added IMG tags. The second-generation TRCP was thus implemented in HTML over HTTP in 1993. What was amazing to many web developers was the enormous worldwide popularity of this website. When it officially ended in 2001, the Washington Post wrote a mock obituary.
Motivated by the notoriety of the web version of the TRCP, copycat web developers came out of the woodwork to achieve their fifteen minutes of fame. I provide two from my digital archives, below:
But of course the matter couldn't end there, either. Interpol, the international paper tiger of law enforcement, enters the fray by issuing a "red notice" on Assange (see Figure 2) who was reported to be living in England. The extradition request from the European Union on behalf of Sweden regarding the latter's arrest warrant is binding on the UK, so under pressure Assange is forced to surrender to English authorities while preparing a case to contest extradition to Sweden on the sex charge. This part of the script is reminiscent of James Cagney's role in Public Enemy.

FIGURE 3: The Online Lizard: no need for rapid frame grabbing here – he/she moves very slowly (circa 1995)
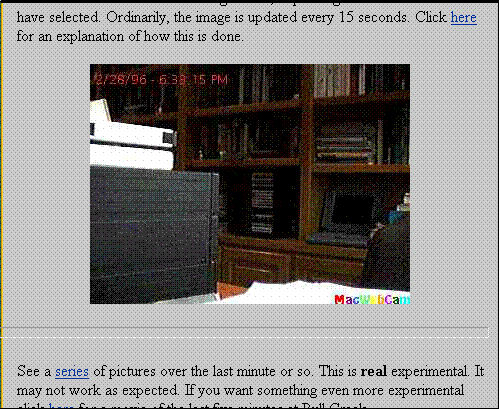
FFIGURE 4: The Empty Nest Online: The office that was usually empty (circa 1996)
By 1995, the world of gratuitous online interactivity was approaching puberty. (Incidentally, my apologies for the poor quality of graphics – but remember this was the era of Windows 3.1 running atop DOS.These screenshots were probably taken from my OS/2 workstation – those were the days!)
And all the while Wikileaks continues to post new cables (see Figure 3) and there was no shortage of European DNS and hosting services (e.g., wikileaks.nl, wikileaks.de, wikileaks.fi). What is remarkable in this cyber battle-of-wits was that it all unfolded so quickly. This is security theater at its best!
As I mentioned, some of the early commentators (including myself) were pretty critical of this online junk. The Trojan Room Coffee Pot may surely be justified as a proof-of-concept prototype. I remember thinking at the time just how clever that was. I hadn't seen anything like it, and was inspired to duplicate it. However, unlike thousands upon thousands of others, I had the good sense to keep my experiments off the publicly accessible web. At least most of my experiments remained private.
By 1995 Alta Vista , the hottest search engine around at the time, indexed 21,000,000 homepages. Even in those early days, things were out of hand, and gratuitous content was taking its toll on bandwidth. Searches became slower and less relevant, and the web became proliferated with “distractions.” In response, I wrote the following in a column in 1995:
“ Once the novelty wears off, the first question of any technology is always "Where's the beef?" -- Where are we headed? Our cultural compass heading setting isn't at all clear. Driven by the glitz and glamor of cyberspace, businesses and individuals are proliferating homepages by the tens of thousands each month. Increasing numbers seem to have no particular objective in mind other than (a) fear of either being ignored or perceived as out of synch with high technology, (b) basic self-indulgence, or (c) blind faith in the recommendations of energetic young techies. ”
Nearly twenty years later, the same holds true. Most of the Internet content remains unimportant and inconsequential. However, technology saved the day in at least two fundamental ways. First the bandwidth is many orders of magnitude greater today than it was then, so the download speeds are not particularly problematic and the access of worthless content doesn't affect us as much. Second, the search engines are way more sophisticated enabling us to more tightly control the searches. Bottom line: the ratio of valuable to invaluable information on the Internet remains low.
For your consideration, I close this column with the same words I used nearly twenty years ago. Perhaps some of you may find it useful in reflecting on your organizations current web presence.
“Don't get me wrong. This revolution in cyberspace is the most important computer revolution since the microcomputer. It will forever change the way we do business, learn, communicate, entertain, and socialize. But each of these changes will take place at different paces and have different importance for different groups. This feeding frenzy approach to Web presence which we're now engaged in is not the way to go about developing cyberspace. At this moment, the digital fly in the ointment is mediocre multi-media, as personified in the vanity homepage.
“Of course the great social cost is the diffusion of the content- rich amidst the content-free. And the great technological challenge will be to provide the appropriate filters so that we can automate the process of separating the two and thereby find the former while avoiding the latter. Without this filtering technology, the Web won't be any more sustainable than water power.
“This challenge will be have to be borne by successive generations of future search engines like Alta Vista mentioned above. This is where Web technology will ultimately prove itself - where the rubber meets the road on the information superhighway as it were. But, I'm getting ahead of myself, for that's the subject of my next column.” (May, 1996)