



 accesses since July 23, 2012
accesses since July 23, 2012
 copyright notice
copyright notice
 link to published version: IEEE Computer, September, 2012
link to published version: IEEE Computer, September, 2012




 accesses since July 23, 2012
accesses since July 23, 2012
Legend has it that the first description of the technique of phishing dates back to a 1987 presentation to an Interex conference by Jerry Felix and Chris Hauck. Within ten years the technique was informally named phishing. That was eons ago in IT years – plenty of time to evolve into new and mysterious techniques. So why is it that we are still trolling for the bottom feeders of the Phishing world?
Let's put this in perspective. In 1987, Microsoft had just released Windows 2.0 as their latest “killer” DOS shell. The newest Intel CPU offering was the 386. Morris hadn't launched his worm yet. The Top-40 hit on some charts was Ben E. King's “Stand by Me.” The big TV premiere of the year was “Married with Children” on the new Fox network, and Seinfeld was still a dream for Jerry. We're talking a long time ago. And through all that time we're just now seeing the last of the Nigerian 419 scam. Where is all the e_criminal talent? We seem to be regressing here.
I offer the following modest examples in support of this claim. We begin with the cryptic phishbait in Figure 1. Clearly this minimalist offering is motivated by some serious cyber-illiteracy. Even on the face of it, this is a paradigm case of “phatuous phish bait:”
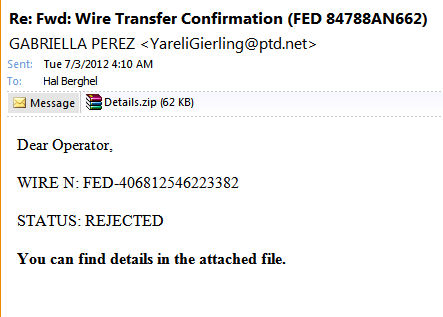
Figure 1: Phatuous Phish Bait
But that’s only the surface. A quick glance at the following email header reveals:
Received: by …. (Postfix) id 4FDB9C73EB; Tue, 3 Jul 2012 06:29:46 -0400 (EDT)
Delivered-To: ….
Received: from [186.113.217.18] (unknown [186.113.217.18])
Received: from [186.113.217.18] by smtpin.ptd.net; Tue, 3 Jul 2012 06:10:19
-0500
Message-ID: <B6796796E5B6796EC8BD3EC8B6710109@AWDn>
From: GABRIELLA PEREZ <YareliGierling@ptd.net>
Subject: Re: Fwd: Wire Transfer Confirmation (FED 84788AN662)
Date: Tue, 3 Jul 2012 06:10:19 -0500
First off, the email source (186.113.217.18) is assigned to an ISP in Columbia while the registrar of record for ptd.net is the internet support service, Tucows.com, which is far too big of a company to cooperate with Columbian ISPs on phish scams. Predictably, an email validation test on YareliGierling@pdt.net yields a 550 error: Sorry, no mailbox by that name
I next offer Figure 2 for your consideration. I've received literally hundreds of these bogus UPS notifications in the last few months – I'm about to drown in digital brown at this point. Take a look at this absurdity. Note that the target is {mailto_username}@{mailto_domain}. C'mon script kiddies, learn about the operation of scripting variables before you use them. Note also that the tracking number link to the malware that starts the infection cycle is startupwordpresstoday.com/spss.html. Now what is the chance that UPS will store their tracking number database on startupwordpresstoday.com which, incidentally, is registered to a Houston P.O. box of a bogus Hotmail account holder)? Call me crazy, but I have a hunch that UPS doesn't use hotmail account holders as their registrars of record. As an aside, all links on the page but the last point to the same malware – a technique which, for want of a better phrase, I'll call phishing by snaglining. By the time that this sub-cerebral phishing effort reached me, the DNS records had already been pulled and the domain name appeared on several blacklists.
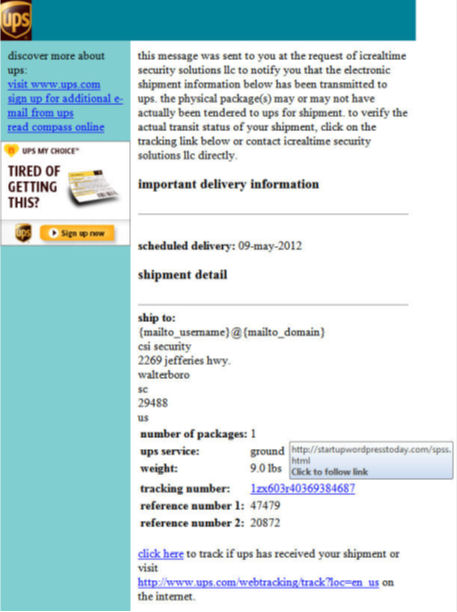
Figure 2: Spray-n-Pray with ‘Snaglining'
Consider the Bulgarian contribution in Figure 3. Although the phish bait came from Sofia, the link reveals that the server that plants the malware is a legitimate automobile dealer in Canada. While the bait itself has little going for it, the person who hacked into the automobile dealer’s server scores higher marks for skill. By the time that the email reached me, some attentive IT person had removed the malware executable from the car dealer’s website – that’s a good thing - but they left the hacker’s directory structure intact, presumably for further investigation.

Figure 3: Chevrolet Phishing Tackle
For the most part, current phish bait stinks. It’s too brutish and lacks any semblance of creativity or sophistication. This betrays a serious dumbing down of phishing generally, which now seems to be almost exclusively in the hands of unenlightened script kiddies. This wasn’t always the case. Five to ten years ago I would receive a continuous stream of grist for my network forensics students’ lab assignments. The latest offerings are too lowbrow for even neophyte students.
To illustrate, consider the following old school classic phish bait in Figures 4a and 4b. This is some bait that the serious undergraduate can get their hands around. Note the creative use of an image map with non-mnemonic filename as the link’s anchor, the stealthy UNIX subdirectory name (…) to avoid the computer owner’s suspicion, the gratuitous hidden text (white on white) to fool email software’s Bayesian analyzer. This is phish bait with pedagogical value, unlike it’s unworthy successors.
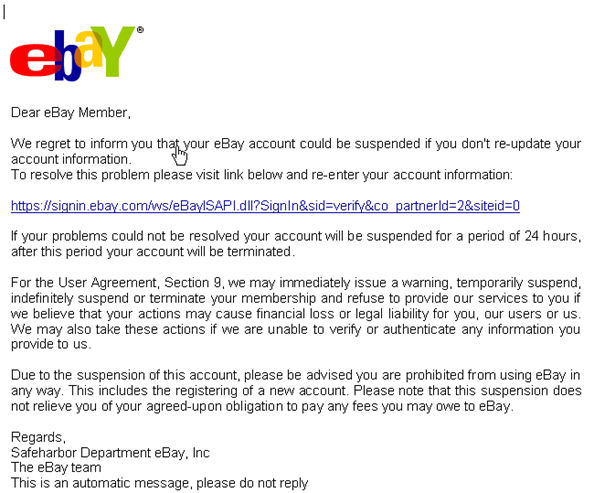
Figure 4a: Classic Phish Bait circa 2005
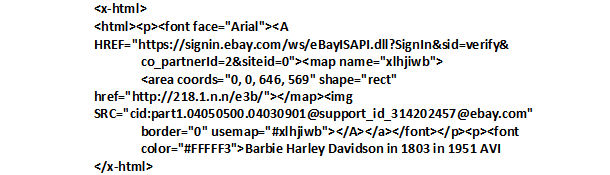
Figure 4b: HTML of 4a
Whatever happened of the skillful hackers of yore who gave the world techniques like those in Figure 4 – and script embedding, domain and URL spoofing, ASCII character convolutions, Unicode/escape encoding, as well? Few ever got prosecuted much less convicted. This lost generation of phishers left an e_crime void that has been filled by merchants of mediocrity.
A reference to the Felix and Hauck report, “ System Security: A Hacker's Perspective,” is available online on the Interex bibliography at http://www.peterjbentley.com/bibliography.pdf . The evolution of phishing is described in http://www.brighthub.com/internet/security-privacy/articles/82116.aspx and also to the Wikipedia entry.
Get your phish groove on by participating in the new Out-of-Band SportPhisher of the Year Tournament for the best and worst phish bait of the year. Send screenshots of the phish bait and justification why you think this candidate is a winner to me at hlb@computer.org . Hang on to the actual email, for I'll request the actual email for the finalists for analysis. If your selection is selected, you'll be credited for the submission (or you may retain anonymity – your call). Send screenshot of the phishbait and your justification of why you think this is a winner (or loser) to me by November 1, 2012.