 published version: Communications of the ACM, Dec. 2007
published version: Communications of the ACM, Dec. 2007 copyright notice (preprint)
copyright notice (preprint)
 published version: Communications of the ACM, Dec. 2007
published version: Communications of the ACM, Dec. 2007





 accesses since September 8, 2007
accesses since September 8, 2007
Hal Berghel
ROOM KEYS THAT AREN'T
A few years back local law enforcement brought an interesting question to one of my labs: Why were hookers, tweakers, and thugs carrying around pockets full of hotel room keys? Busts of the local street ciminals were producing a virtual cornucopia of hotel room keys of all shapes and sizes. In addition, the cops found gift cards, rewards cards, player's cards, calling cards, membership cards -virtually everything that had a magnetic stripe on it.
It turned out that the magnetic stripes contained credit card information. The source data was either "skimmed" or "duped" from the original card and then recorded on the magnetic stripe of hotel room keys with widely available card reader/writers . Tthere was a burgeoning industry in this form of credit card fraud, with well-organized groups working within a moderately well-defined chain of command. The bottom-feeders were collecting the information and passing it up to the criminal leadership who then either imprinted the account information on the room keys, brokered the account information over the Internet, or traded the information with other criminals
The most prevalent threat was skimming since it doesn't require separating the card from the owner. This produces a much longer useful life for the credit card information - by the time the user or credit card company discovers that the card has been compromised, the thieves have already moved on to the next victim. A common skimming tactic is to "double swipe" - once at the point-of-sale terminal, and once on a hand held device. Current battery powered skimmers about the size of a thumb, cost less than $500, can hold thousands of credit cards, and have USB interfaces for ease of downloading. At the time of this investigation, local law enforcement discovered that most of the skimming was taking place in ethnic restaurants. The wait person could easily conceal the skimmer in their apron or a pocket and complete a shift with dozens to hundreds of credit cards skimmed.
The first batch of discovered hotel room keys produced some confusion. Local law enforcement was not used to seeing so many hotel room keys on anyone. But after the credit card information was discovered, the proverbial light went on. In the State of Nevada it was illegal to possess more than two credit/debit cards in another's name. The criminals new if they were found with actual credit cards, they would be arrested. So their workaround was to copy the magnetic information onto the surrogate cards to avoid detection and detention. The jig was up when law enforcement found out what kind of information was on the hotel room key magnetic stripes.
DIGITAL CSI
When Deputy Chief Dennis Cobb brought this caper to our attention, he challenged us to develop a hand-held scanner that could detect whether anomalous data was on a magnetic stripe without actually reading or storing the data. Legally, knowing *that* there is credit card information on a hotel room key is a very different piece of evidence than knowing *what* credit card information was on it. Our first challenge was to define what it was to be an anomaly in this context.
When IBM created the magnetic stripe card technology in the 1960s they allowed different industries to influence the format of the three tracks on the stripes. The airlines industry got first pick on track one, where the banking community defined track 2 and the savings/thrifts defined track 3. A de facto standard recording density for most industries and applications is 210 bits/in for all 3 tracks. Track 1 is a 7-bit format, while tracks 2 and 3 are 5-bit. Since track 1 has the larger character set, only it has alphanumeric-cum-special character capability. Tracks 2 and 3 are limited to the ASCII hex 30-3f characters. Of course, these formats could vary widely by application.
For brevity, we'll confine our present attention to the financial industry, and more specifically, to credit cards. There are several ISO/IEC standards that apply to magnetic stripes on credit cards, especially ISO/IEC 7810 - 7813. The related specification, ISO/IEC 4909:2006, applies to the thrift industry and a similar discussion that is beyond our present focus would apply to it. These standards specify the physical characteristics, layout, track densities and formats, merchant ID codes, etc. for financial transactions cards. Of specific interest to us were ISO/IEC 7813:2006 relating to the data structure and content of magnetic tracks 1 and 2.
Of course there is considerable variety in the data specifications between credit card issuers that have to be accommodated when scanning the card. We'll deal with a generic case, below:
| field | length | definition | example |
|---|---|---|---|
| 1 | 1 | start sentinel | % |
| 2 | 1 | format code (alphabetic) | B=format code for bank/financial industry |
| 3 | <=19 | primary account number | 121741512345678 |
| 4 | 1 | field separator | * |
| 5 | <=26 | holder's name | sutton/willie |
| 6 | 4 | expiration date (MMYY) | 0503 |
| 7 | 3 | service code | 101 |
| 8 | 5 | PIN Verification Value | 51395 |
| 9 | var | discretionary data | |
| 10 | 1 | end sentinel | ^ |
| 11 | 1 | Longitudinal Redundancy Check Character | 1 |
Myriad subtle differences may be found within this generic scheme. Again, for brevity we’ll only mention that they, too, may be used to authenticate the information as belonging to a credit card. The over-arching idea behind this analysis is that the more information on the magnetic stripe that conforms to credit card formats, the higher the probability that this information is a credit card record. The goal is to provide law enforcement with immedidate feedback that produces probable cause for further forensic investigation.
The figures below illustrate some of the features of our scanning system, CardSleuth (pat. pend). Note that in Figure 1 only the red stop light is indicated (accompanied by sound), meaning that the mag stripe scanned is not what would have been expected. In this case, we were looking for hotel room key information on the mag stripe, but the red light indicates that we found a credit/debit card information. This satisfies our requirement of reporting "that" rather than reporting "what." Figure 2 is the "forensics" view of the mag stripe information - normally seen by detectives after an arrest/court order/ etc. has been issued. This confirms the format of the data described above. Figure 3 reports the result of looking for a hotel room key and finding it.
Figure 1: View from hand held scanner: looking for hotel room key information but finding credit card information.
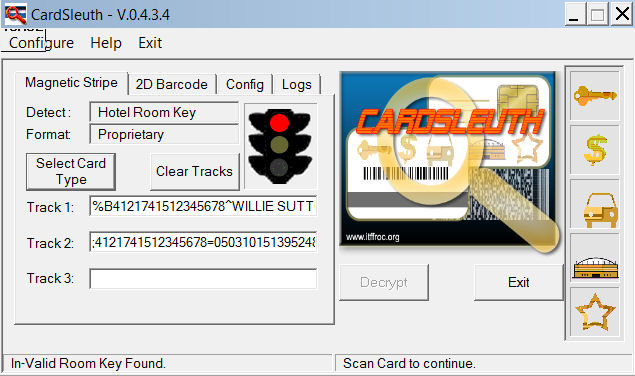
Figure 2: : Forensic view of looking for hotel room key information but finding credit card information.
The notion of anomaly deserves further explanation.. Recall that our goal was to detect anomalies, one example of which is credit card information on a hotel room key. Of course, the converse would also be an anomaly. Though we haven't detected this as yet, it's entirely possible that criminals could put hotel room information on a credit card so that they might conceal that they have access to a victim's room. Again, the criminal reasoning would be similar to the “more-than-2” case: if criminal activity were suspected in a hotel room, a holder of a hotel room key to that room might be suspect. But what is the likelihood that an investigator will swipe a worn, embossing-reduced credit card in a hotel room key?
CardSleuth is designed to look for such anomalies on a variety of cards with magnetic stripes, barcodes, RFID, cards, etc. The Cartesian product of these media types against function or use (e.g., credit/debit/ATM cards, driver's licenses, sundry identification cards, passports, visas, room keys, benefit transfer cards, etc. significantly complicate the notion of "anomalous." In this column, we discuss just one case.
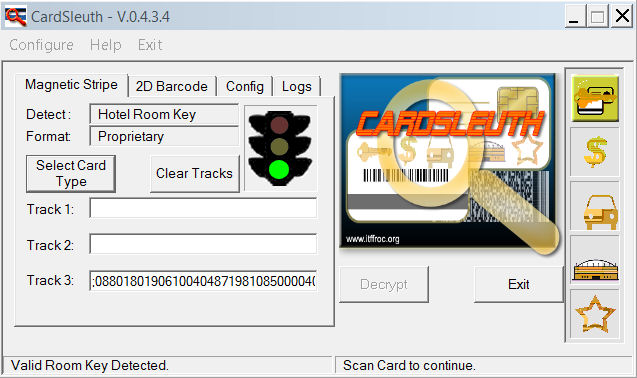
Figure 3: : Forensics view of looking for and finding a legitimate hotel room key
THE REST OF THE STORY
The toothpaste is pretty much out of the tube regarding the old hotel room key card scam in our municipality, but it’s not dead yet. Not all municipalities and their law enforcement have the same levels of awareness of this exploit. Further, variations abound. The most interesting aspect of this story was how a law enforcement agency and university research center could cooperate to prevent crime.
In the course of this project we came up with some interesting observations. For one, the entire scam could have been avoided if the scanners were configurable with respect to the level of coercivity on the magnetic stripes. Financial industries use the more persistent and more reliable hi-coercivity magnetic stripes with a flux denisty of 4000 Oersteds. All of the hotel room keys that were provided to us were lo-coercivity (300 Oersteds). The difference in magnetic field strength is easily recognizable by modern electronics. In our case, simply rejecting any credit card information that appeared on a lo-co mag stripe would have prevented the problem from arising in the first place. Note that a “lo-co” block on unattended point-of-sale terminals could have preented this criminal behavior before it got started.
Another byproduct of our work was the prevalence of credit card information on the Internet. At one point we were experimenting with net bots that could look for and report on financial card information on the net. As an aside, I can affirm that this research was of little interest to law enforcement for legal reasons. Ironically, having the ability to find credit card fraud in progress incurs considerable liability to attempt to thwart it which in turn brings in issues of agency, jurisdiction, work flow, and so forth which opens new cans of worms that struggling law enforcement agencies with enormous case loads are ill-prepared to deal with.
Over time, this project has been extended to other identification and card media formats, and functionality that goes beyond law enforcement. The common theme, however, is the detection of anomalous information on widely-used identification and access control media.
CONCLUSION
I would be remiss if I didn’t suggest some guidelines to protect oneself from scams such as that described above. The Department of Justice’s SCAM acronym is appropriate here: be Stingy about giving out personal information, Check personal financial information regularly, Ask for copies of personal credit reports periodically, and Maintain careful records of banking and financial accounts.
For more information about our credit card theft and street urchins story, see Brian Krebs' Washington Post blog at blog.washingtonpost.com/securityfix/2006/03/street_level_credit_card_fraud.html
For the curious, ISO/IEC 7810 documentation may be found on the ISO/IEC/IEC website at www.iso.org/iso/en/CatalogueDetailPage.CatalogueDetail?CSNUMBER=31432&ICS1=35&ICS2=240&ICS3=15. For those who don't care enough to pay for the download, a useful facsimile is available online at the DED Limited website at www.ded.co.uk/magnetic-stripe-card-details.html. ASCIItable.com is a convenient online ASCII table.
Our anti-spoofing technology extended to counterfeit and forged IDs as well. The problem of fungible credentials is discussed in my column in the December, 2006 CACM.
Periodic review of popular government and law enforcement websites that deal with preventive measures for electronic crime and identity theft is definitely warranted, as current loss estimates exceed $100 billion and affect a large percentage of the population. A good start is the Department of Justice website, particularly www.usdoj.gov/criminal/fraud/websites/idtheft.html. Another useful reference is the Internet Crime Complaint Center at www.ic3.gov. A first approximation at securing credit card transactioning may be found in the Payment Card Industry (PCI) Data Security Standard. Version 1.1 (September, 2006) may be found online via www.pcisecuritystandards.org.
Hal Berghel is an educator, administrator, inventor, author, columnist, lecturer and sometimes talk show guest. He is both an ACM and IEEE Fellow and has been recognized by both organizations for distinguished service. He is the Associate Dean of the Howard R. Hughes College of Engineering at UNLV, and his consultancy, Berghel.Net, provides security services for government and industry.